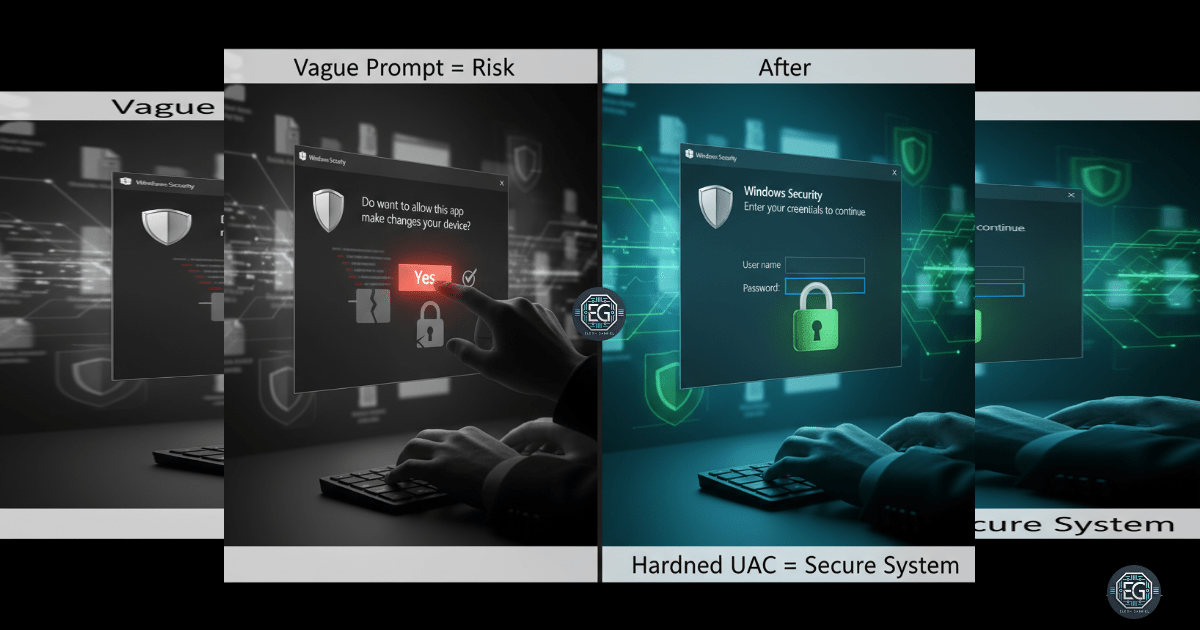
When it comes to system security, one of the easiest attack paths is when users (or even admins) can click “Yes” without thinking. That’s where User Account Control (UAC) steps in. It forces anyone—standard users or admins—to stop, authenticate, and prove they should be making a sensitive change.
For this exercise, I used the Local Group Policy Editor to tighten UAC and make sure credentials were required for all administrative actions. The goal: stop malicious software or unauthorized users from sneaking changes past me.
What I Configured
- Enabled Admin Approval Mode for the built-in Administrator account
- Required credentials for all elevation prompts (not just a quick “Yes” click)
- Forced prompts to appear on the secure desktop to block spoofing attempts
- Ensured installations trigger prompts before making changes
Validation
After applying the policies, I ran an application with admin privileges. Instead of a casual prompt, I was forced onto the secure desktop to enter my credentials. Exactly the behavior I wanted—clear evidence that the system was properly hardened.
Why This Matters
By enforcing UAC through Group Policy, I reduced the risk of unauthorized changes, credential theft, and privilege escalation. Even built-in administrators have to prove themselves before executing sensitive actions. It’s a small step in system hardening, but one that creates a huge barrier for attackers.
For a deeper dive into the exact configuration steps, validation process, and supporting observations, check out my full UAC Hardening Report below. It details every policy path and setting applied, so you can see exactly how this exercise strengthens system security.