Eldon Gabriel
Secure Infrastructure | System Hardening | GRC Strategy
I provide hands-on security implementation and framework-aligned technical controls to harden enterprise systems, investigate incidents, and reduce organizational risk. As an ISC² Certified Cybersecurity Professional (CC) with 120+ documented technical labs and reports, I specialize in transforming complex IT environments into secure, compliant, and resilient infrastructures.
My work is grounded in a "Proof of Work" methodology—executing repeatable, documented security processes that strengthen systems, mitigate vulnerabilities, and support compliance readiness.
What I Bring to an Organization
System Hardening
Advanced Windows and Linux lockdown with automated IP access control. I implement deep-level GPO and Registry restrictions to reduce attack surface and enforce least privilege.
- Server Security Evaluations
- Least Privilege Implementation
- Automated IP Access Control
Network Defense
pfSense orchestration and root-cause network analysis. I identify misconfigurations and unauthorized access to improve perimeter and internal defenses.
- Enterprise IPSec VPN Troubleshooting
- Network Traffic & DNS Diagnostics
- Unauthorized Access Investigation
Operational Resilience
Permanent remediation and risk reduction based on NIST-aligned frameworks. I connect GRC strategy with actionable technical safeguards.
- Bank-Grade Risk Registers
- BYOD & Security Policy Design
- Post-Breach Remediation Strategy
Explore Verified Skills View Technical Portfolio
Foundational Mentorship

George H. Ross
NBC’s ‘The Apprentice’ Judge & Mentor
Instilled a disciplined evaluation of risks and thorough investigative practices essential for proactive threat hunting and forensic accuracy.

Wahida Clark
4x NYT Bestselling Author
Reinforced the importance of clear communication and technical storytelling to translate critical risks into actionable business insights.
Technical Case Studies
Independent Reports & Public Project Documentation
My expertise is backed by 100+ verified technical labs and reports. Due to non-disclosure agreements and academic integrity pledges (MCSI), detailed lab reports for specific curriculum milestones are available only upon direct request for verified professional inquiries.
Let's Secure Your Infrastructure
Ready to deploy NIST-aligned hardening or request a private technical review? Let's connect.
Contact Me for a Consultation
Bridging IT Fundamentals to Cybersecurity Mastery
Resolving AWS MGN Agent Removal Issues After VMware to EC2 Migration
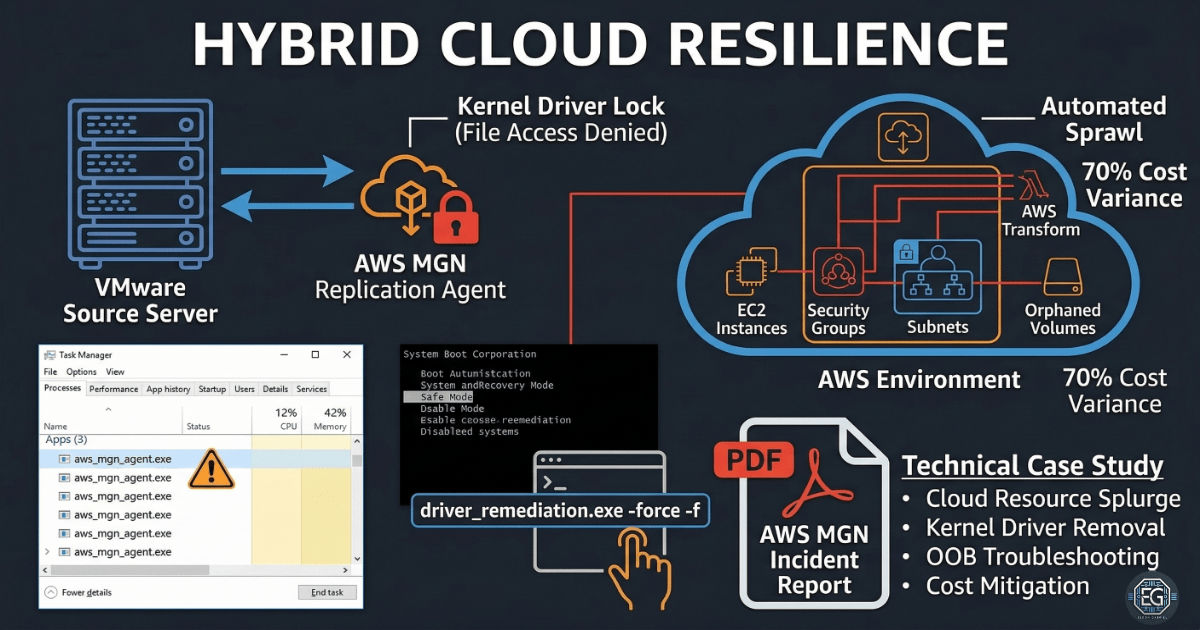
A practical troubleshooting case study on migrating VMware virtual machines to AWS EC2 and resolving kernel driver removal issues from the AWS Application Migration Service.
Bypassing Firmware Locks for Nested vSphere 8 on Ryzen 6000
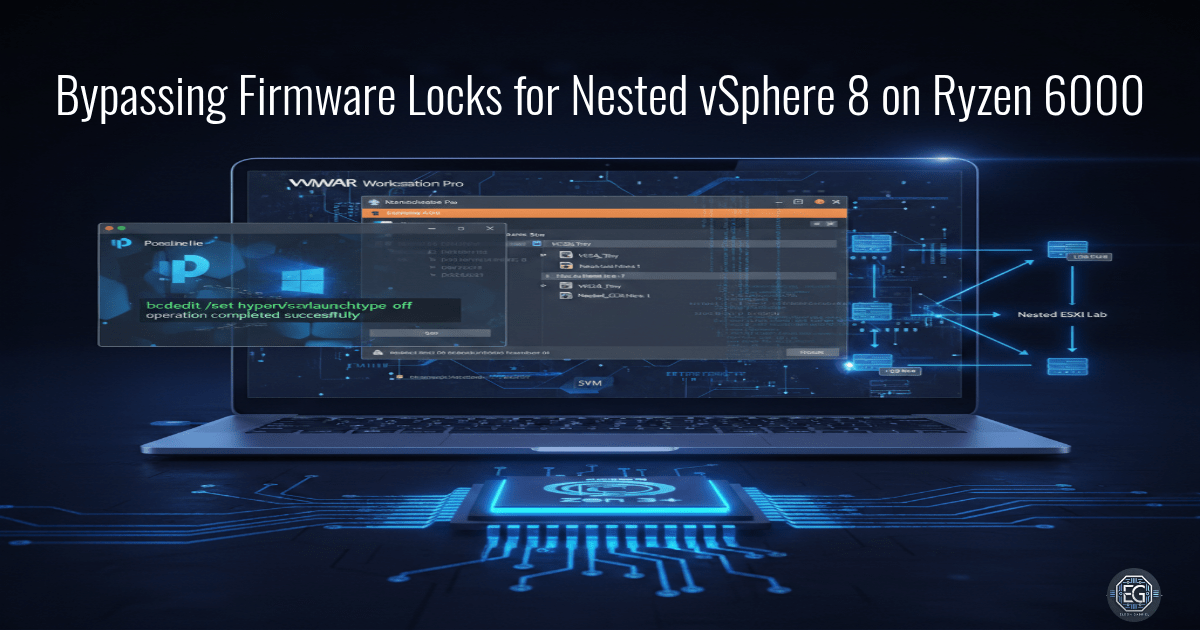
A technical deep-dive into enabling nested virtualization on restricted AMD mobile platforms by bypassing OEM firmware locks and Windows 11 VBS.
Reverse Image Search in OSINT Investigations
Performed reverse image searches to analyze images, extract metadata, and practice OSINT skills for verifying authenticity and gathering intelligence.
UTM Kali Linux Shared Folder Guide: Persistent File Sharing for Cybersecurity Labs
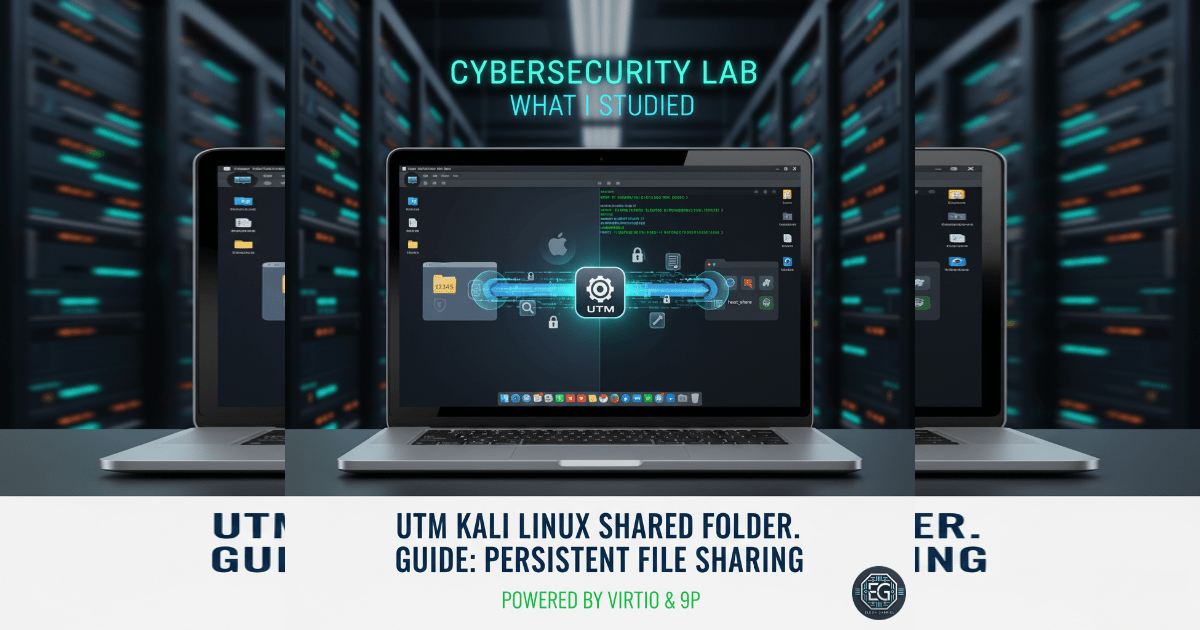
Configured a persistent shared folder between macOS and Kali Linux in UTM to enable reliable cross-platform file transfer for cybersecurity lab environments.
Email Pattern Recognition with OSINT
A hands-on OSINT exercise focused on identifying and validating target email addresses using public PDF documents and email verification tools.
Deploying User Session Lock Policies on a Single Machine

Configured Local Group Policy to enforce automatic session locks, improving Windows endpoint security.
Deploying User Rights Policies on a Single Machine

Configured User Rights Assignment policies via Local Group Policy to enforce least privilege and secure Windows endpoints.
Securing WinRM Configuration with Local Group Policy

Deployed a Local Group Policy Object to securely configure Windows Remote Management (WinRM) for encrypted, authenticated remote administration.
Deploying Local Group Policy to Harden SMB Sessions

A hands-on walkthrough of using Local Group Policy and the Windows Registry to enforce SMB signing, disable SMBv1, and reduce the risk of credential theft and session hijacking.
Deploying Local Group Policy to Strengthen Windows Security

Hands-on exercise applying Local Group Policy settings to harden a Windows 10 workstation and improve system security posture.

