2026
Bypassing Firmware Locks for Nested vSphere 8 on Ryzen 6000
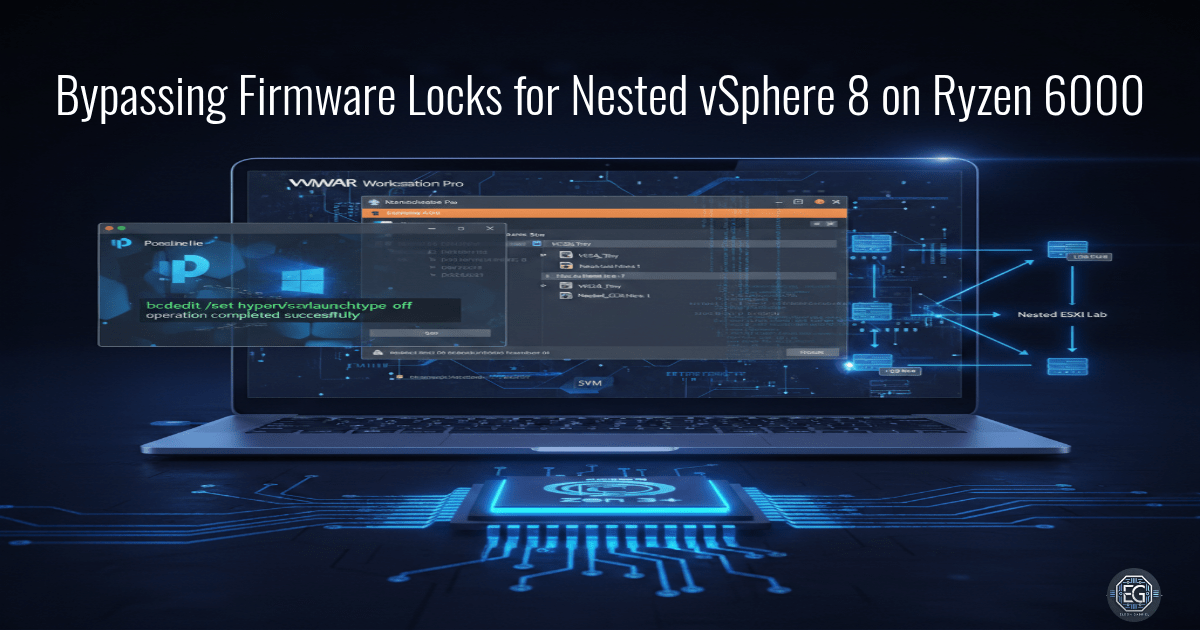
A technical deep-dive into enabling nested virtualization on restricted AMD mobile platforms by bypassing OEM firmware locks and Windows 11 VBS.
2025
Reverse Image Search in OSINT Investigations
Performed reverse image searches to analyze images, extract metadata, and practice OSINT skills for verifying authenticity and gathering intelligence.
UTM Kali Linux Shared Folder Guide: Persistent File Sharing for Cybersecurity Labs
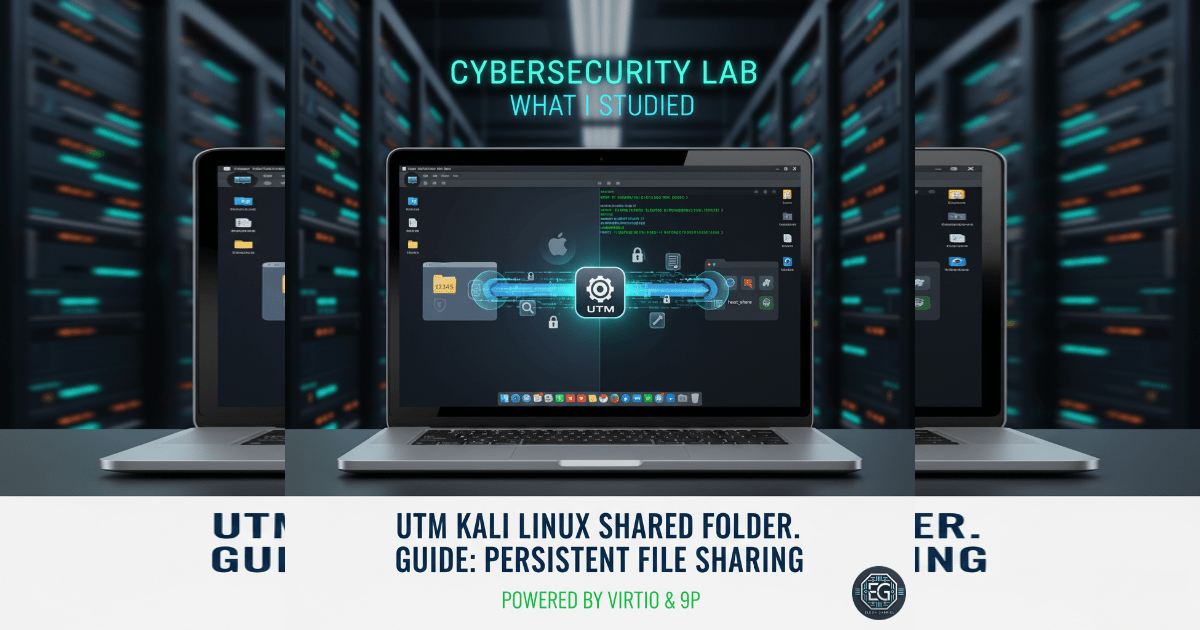
Configured a persistent shared folder between macOS and Kali Linux in UTM to enable reliable cross-platform file transfer for cybersecurity lab environments.
Email Pattern Recognition with OSINT
A hands-on OSINT exercise focused on identifying and validating target email addresses using public PDF documents and email verification tools.
Deploying User Session Lock Policies on a Single Machine

Configured Local Group Policy to enforce automatic session locks, improving Windows endpoint security.
Deploying User Rights Policies on a Single Machine

Configured User Rights Assignment policies via Local Group Policy to enforce least privilege and secure Windows endpoints.
Securing WinRM Configuration with Local Group Policy

Deployed a Local Group Policy Object to securely configure Windows Remote Management (WinRM) for encrypted, authenticated remote administration.
Deploying Local Group Policy to Harden SMB Sessions

A hands-on walkthrough of using Local Group Policy and the Windows Registry to enforce SMB signing, disable SMBv1, and reduce the risk of credential theft and session hijacking.
Deploying Local Group Policy to Strengthen Windows Security

Hands-on exercise applying Local Group Policy settings to harden a Windows 10 workstation and improve system security posture.
Stabilizing Remote Desktop Connections Across Platforms
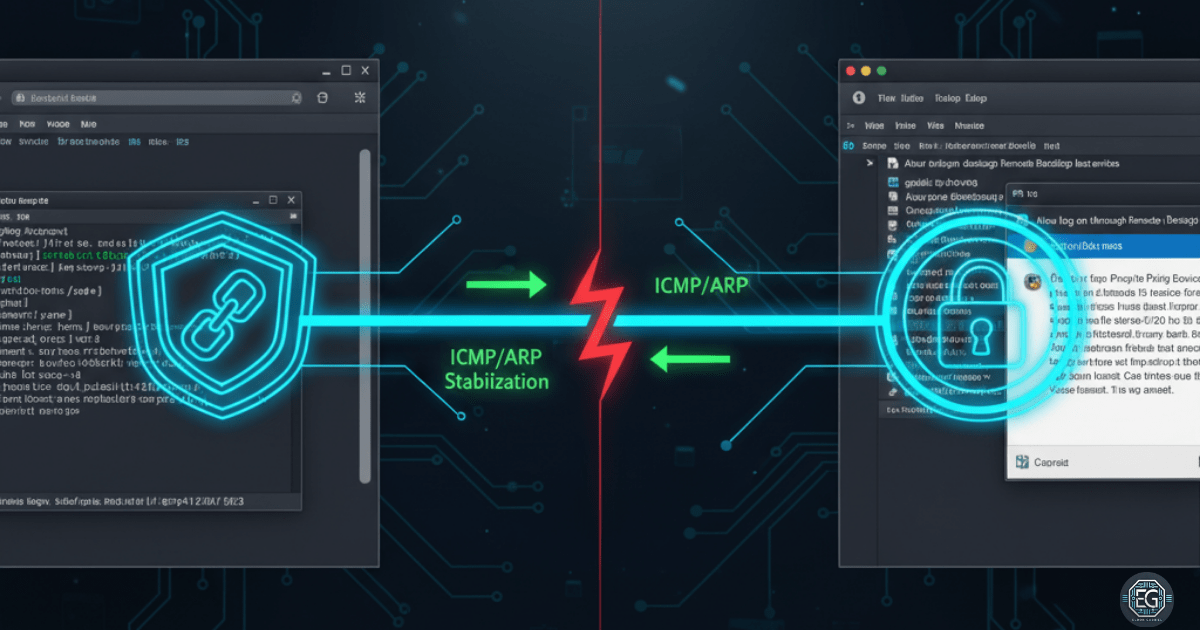
Resolving complex RDP connectivity issues caused by Domain GPO restrictions and virtual network instability in a macOS UTM environment.
Translating Foreign-Language Data in OSINT Investigations
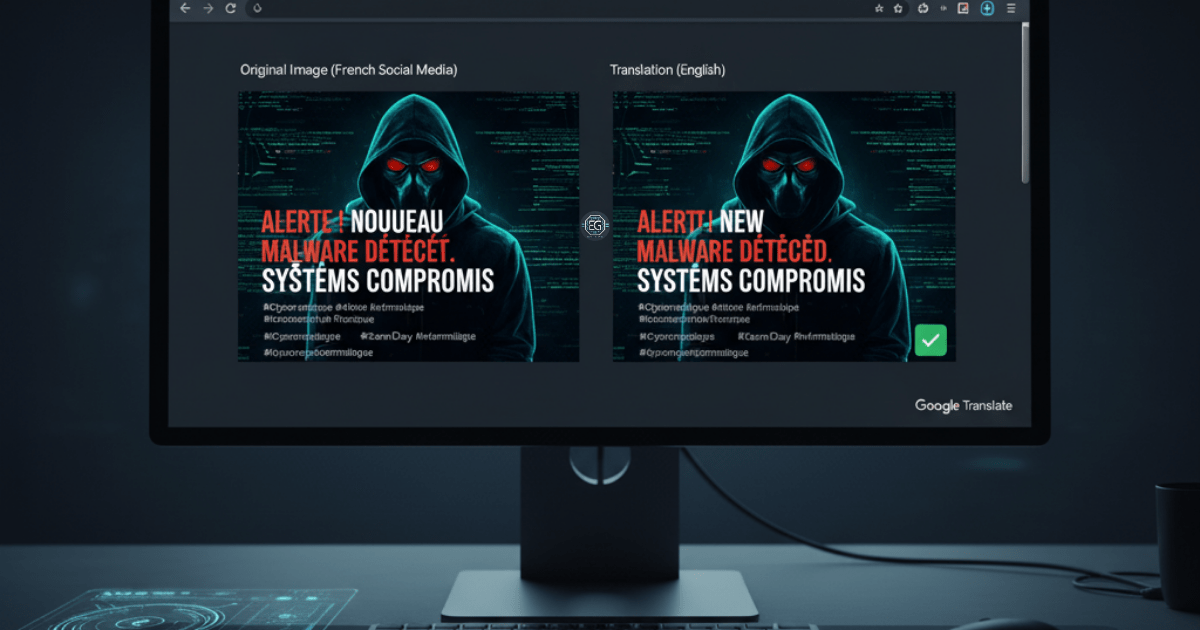
Using translation tools to process and validate foreign-language data from multiple sources including articles, code, images, documents, and webpages.
Hardening Windows Defender on a Single Machine with Local GPO

Using the Local Group Policy Editor to harden Windows Defender by enforcing real-time protection, behavioral monitoring, and restricting user tampering.
Hardening Windows 10 by Restricting Anonymous Connections
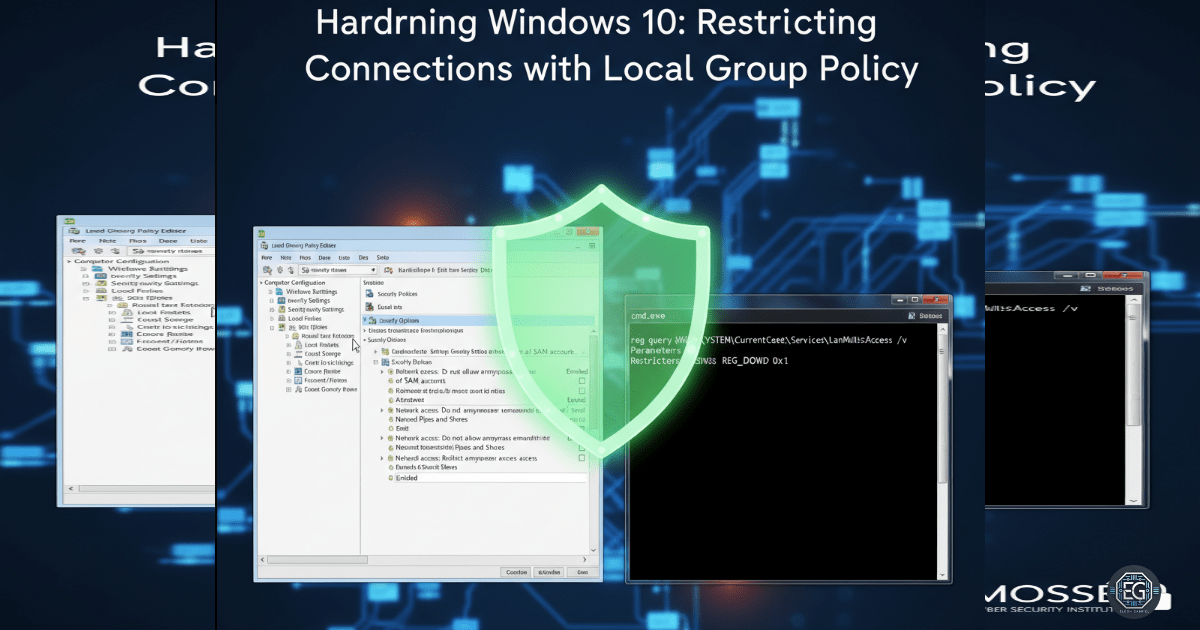
A practical walkthrough on hardening Windows 10 by restricting anonymous connections through Local Group Policy, blocking null session enumeration of shares and named pipes.
Hardening Windows 10 with Password & Account Lockout Policies
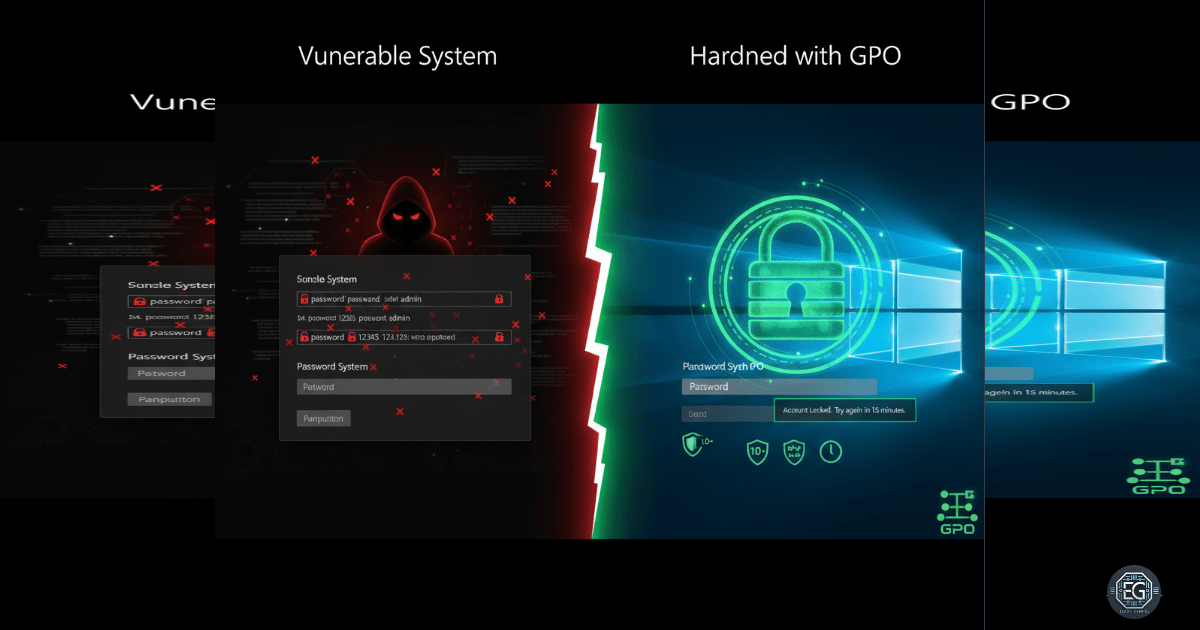
A hands-on walkthrough of configuring Windows 10 Local Group Policy to enforce strong password and account lockout settings, defending against brute-force and password guessing attacks.
Enforcing Windows Patching Policies with Local Group Policy
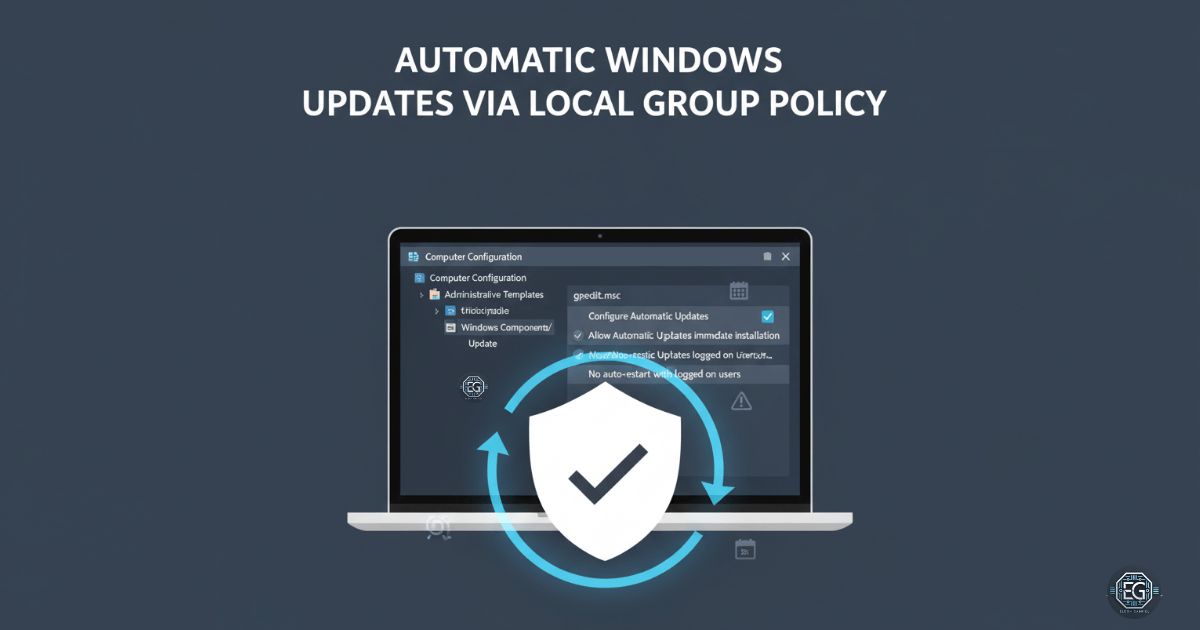
A simple walkthrough showing how to use Local Group Policy to keep Windows 10 patched and protected against new threats.
Apply Best Practices to Harden Microsoft Edge Against Known Weaknesses
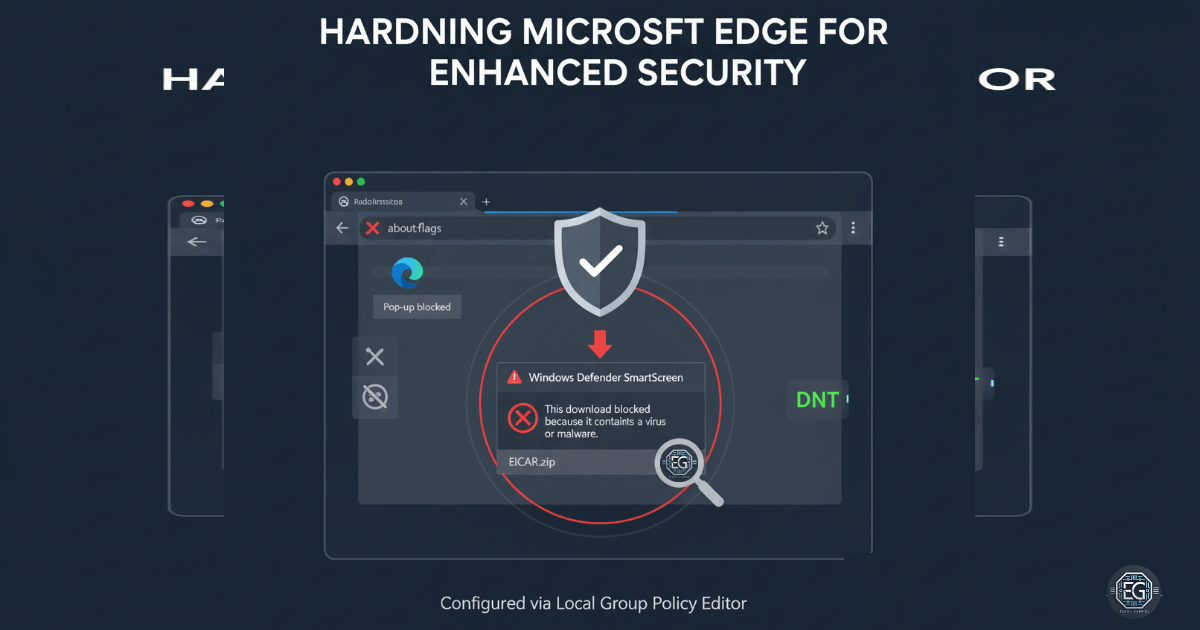
Learn how to harden Microsoft Edge using Local Group Policy to enhance browser security and protect against known vulnerabilities.
Protecting Windows 10 with Hardened UAC Settings
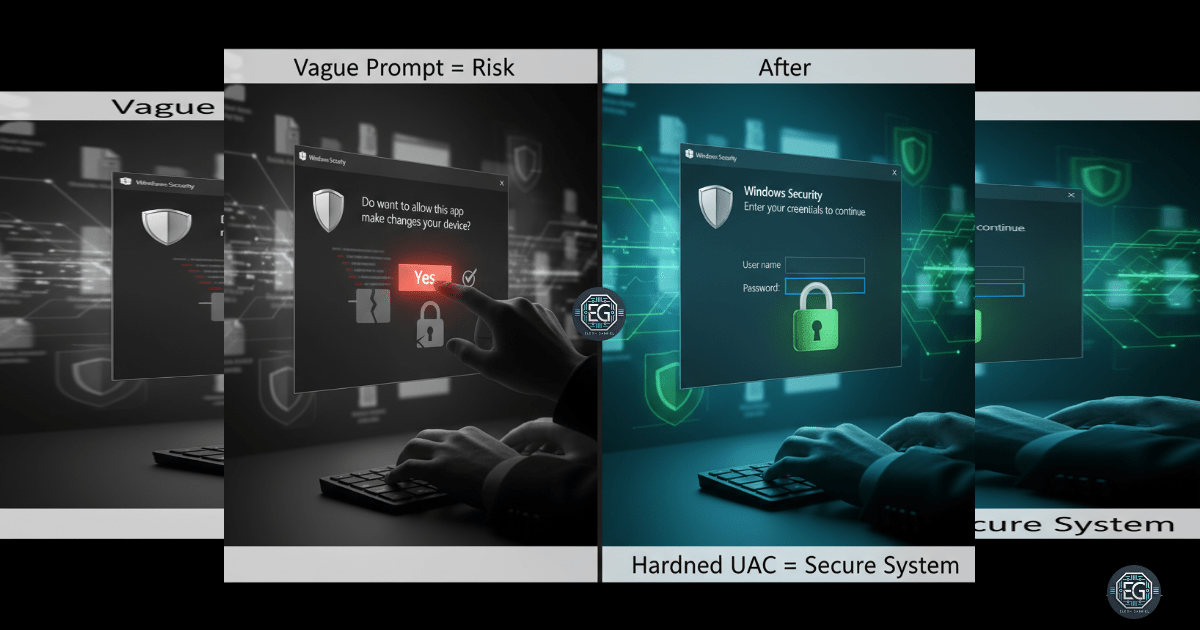
A practical walkthrough on hardening Windows 10 UAC settings using Group Policy to enforce credential prompts and secure desktop elevation.
Protecting Sensitive Folders with Controlled Folder Access via Local Group Policy
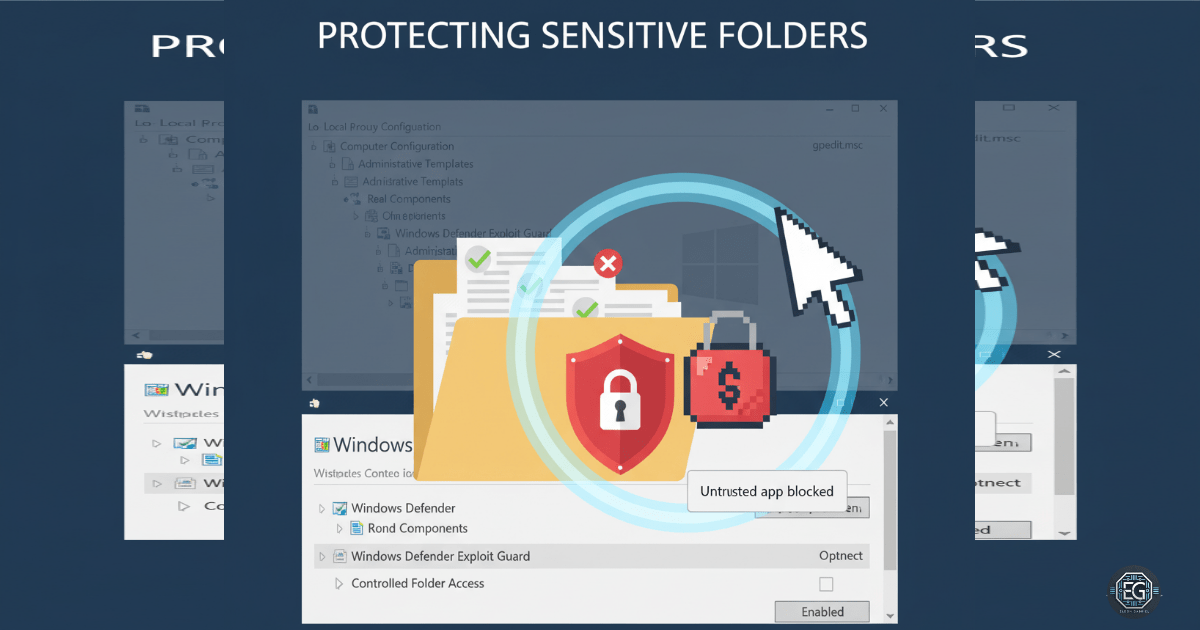
Hands-on experience configuring Controlled Folder Access (CFA) on Windows 10 to protect against ransomware using Local Group Policy.
The Importance of Clear Prompts and Rubrics in Cybersecurity
Why vague instructions create risk and how critical analysis of prompts and rubrics strengthens cybersecurity skills.
Hardening Windows Security with GPO
A hands-on look at securing Windows machines using Group Policy Objects for application control and secure credential entry.
Windows Control Panel Administration: Research, Labs, and Instructor Feedback
Follow-up to my 11 independent Windows administration labs, this report integrates research, video demonstrations, and instructor feedback to highlight clarity, practical application, and professional documentation skills.
Mastering GCP: Windows 10 VM Deployment
An independent lab demonstrating deployment of a Windows 10 virtual machine on Google Cloud Platform, showcasing cloud virtualization, secure configuration, and system administration skills.
Mastering Windows System Administration: 11 Independent Labs

A collection of 11 hands-on labs designed to build Windows administration skills, covering maintenance, troubleshooting, security, and automation — all tested in an AWS-hosted Windows 10 VM.
How Password Managers Strengthen Security and Simplify Credential Management
A professional overview of password managers, their importance, types, and relevance to enterprise security.
File Ownership Recovery in Windows

A concise overview of how to recover file ownership in Windows using built-in tools.
RDP Troubleshooting for AWS Users
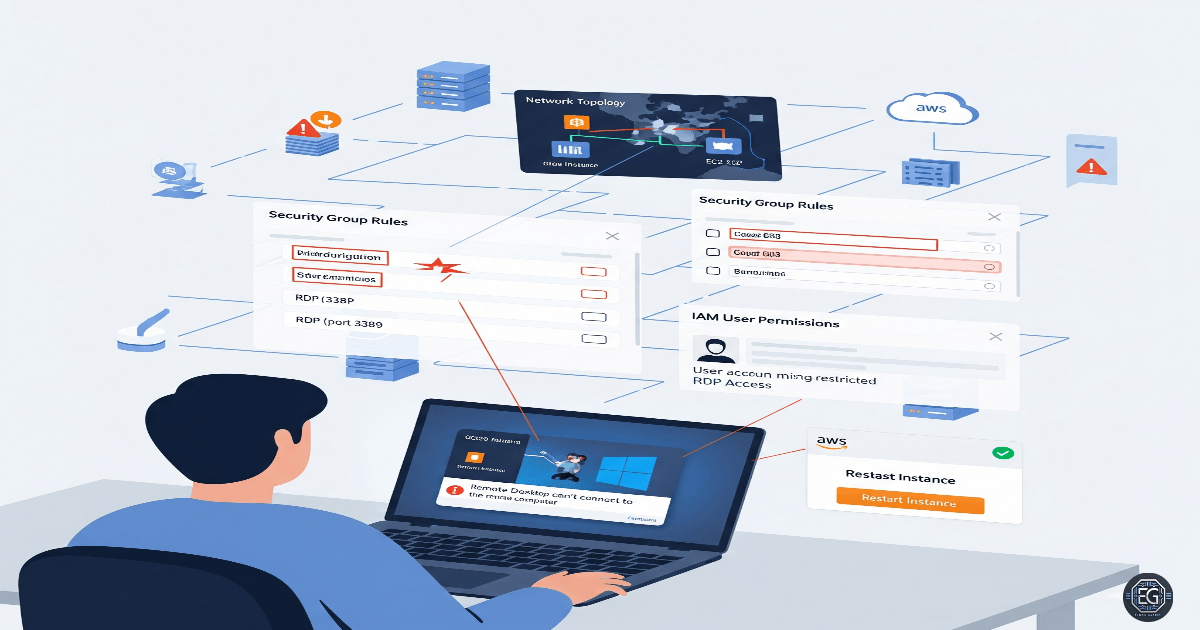
A hands-on guide to troubleshooting Remote Desktop access for new user accounts on AWS-hosted Windows 10 VMs.
Using the Windows Registry to Restrict Untrusted User Accounts

Hands-on exercise in securing Windows endpoints by restricting untrusted user accounts via the DisallowRun registry key.
Monitoring Windows Processes with Procmon: A Practical Guide

A step-by-step guide to using Procmon to capture, filter, and analyze Windows process activity for threat hunting, incident response, and compliance.
Refreshing My Subnetting Skills: From Handwritten Notes to a Full Class C Subnet Report
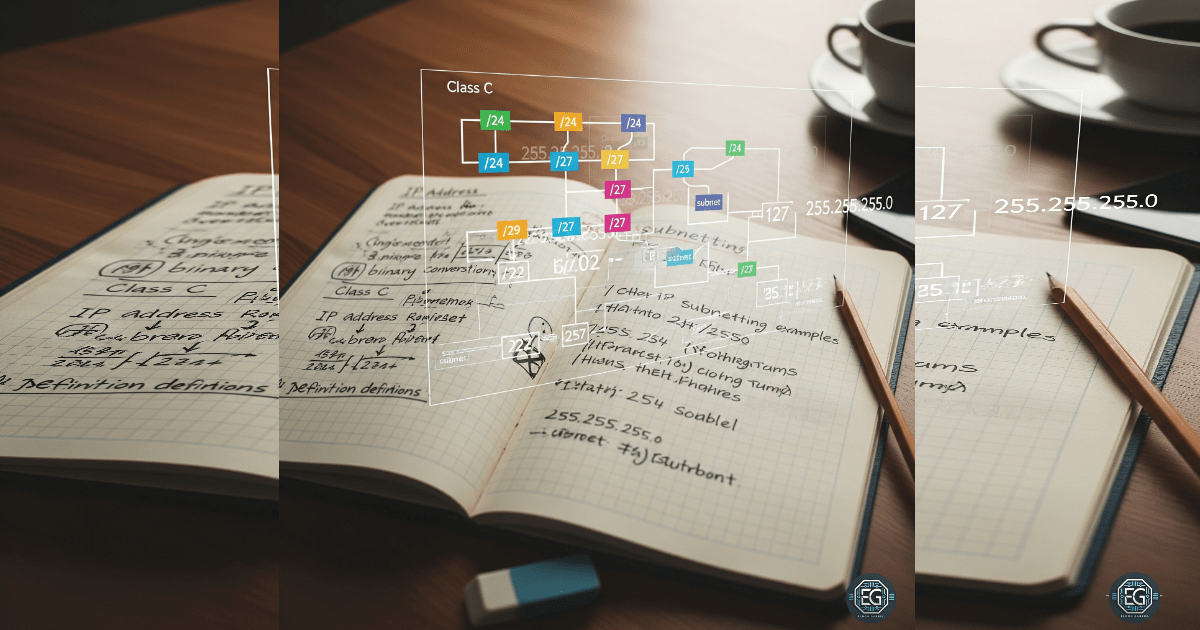
Turning my old handwritten subnet notes into a complete Class C subnet report and a useful reference for labs and exercises.
Securing Sensitive Folders: Lessons in Access Rights and Permissions
Hands-on lab experience in securing sensitive folders and restricting PowerShell, applying least privilege and defense-in-depth strategies in Windows environments.
Blocking SMB Access: Strengthening Network Security with Windows Firewall
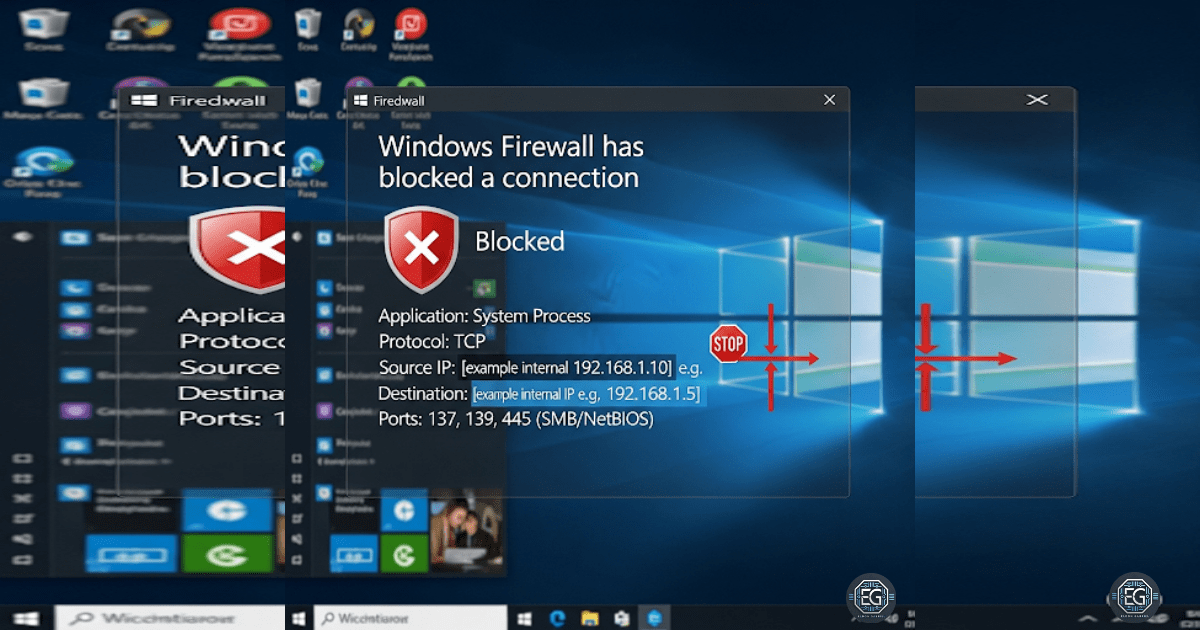
A hands-on guide to turning on Windows Firewall, blocking SMB traffic, and understanding protocol security risks.
Kerberos Explained: Turning Complex Security into Clear Insights
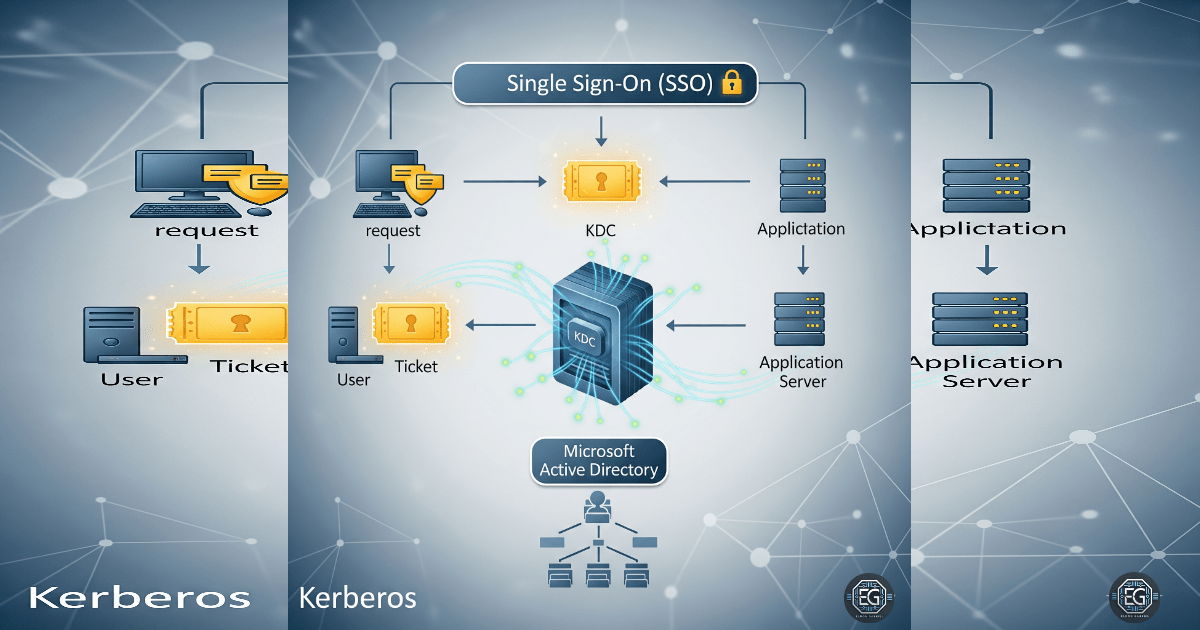
An in-depth look at the Kerberos authentication protocol, lessons learned, and how to communicate complex security concepts effectively.
Mastering Windows OS: Security and System Hardening for Cybersecurity
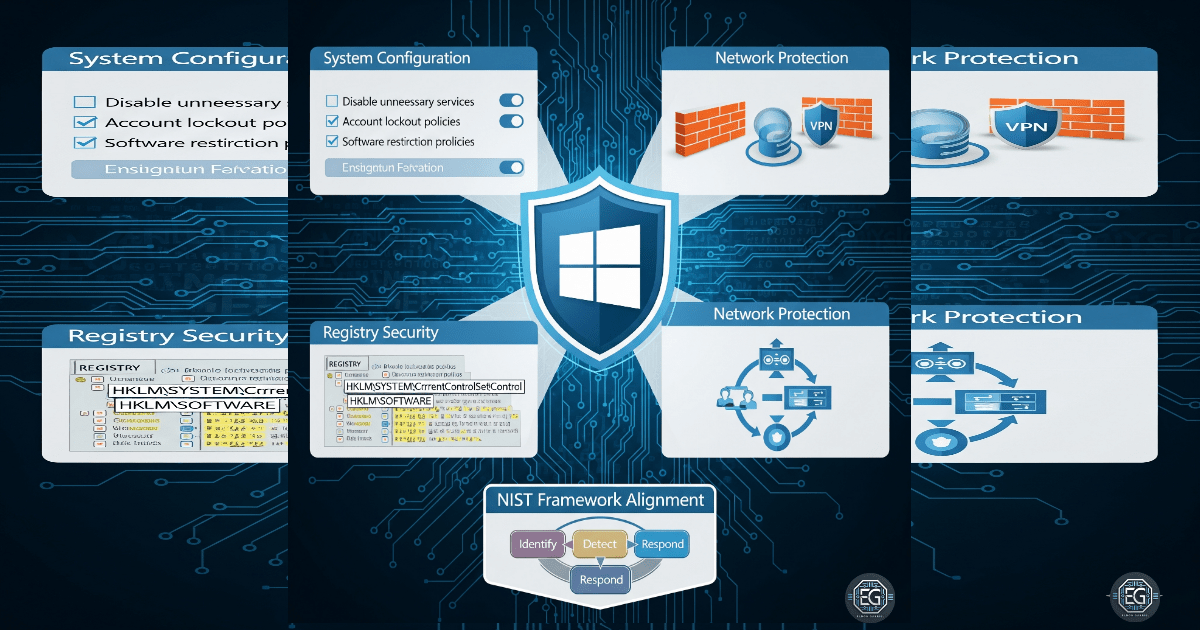
A hands-on guide to Windows OS hardening, covering best practices for system configuration, network protection, and registry security.
BYOD in Organizations: Security, Challenges, and Practical Strategies
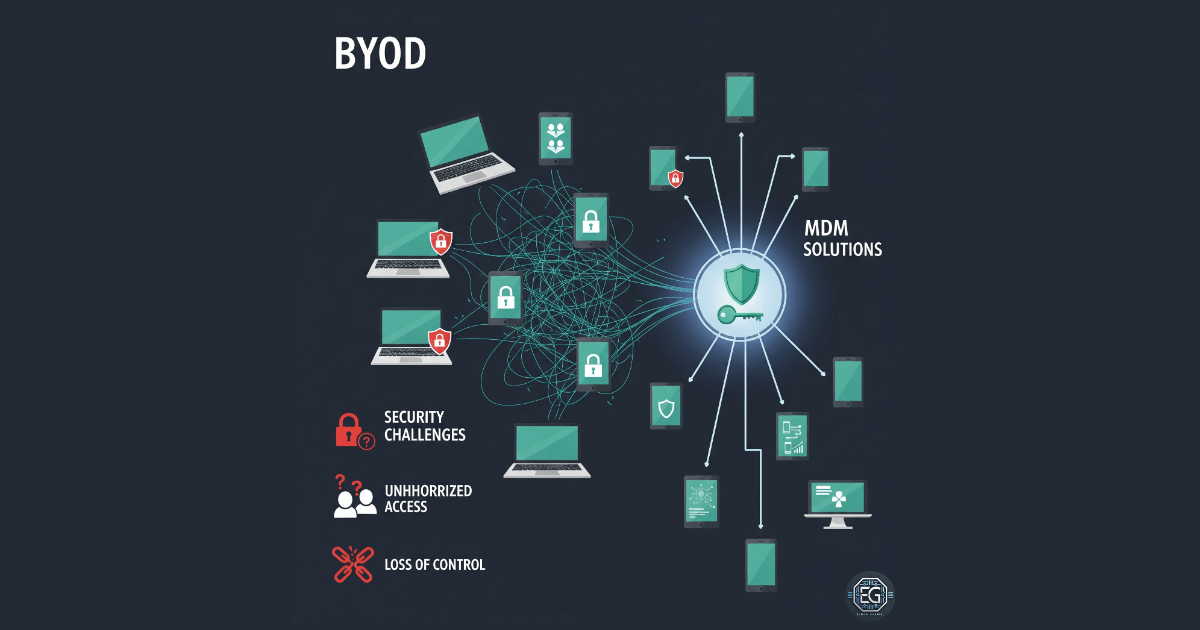
A hands-on exploration of BYOD security, challenges, and practical strategies for organizations, combining MCSI labs with University of Colorado coursework.
How I Built a Professional Cybersecurity Report Template
Building a reusable cybersecurity report template was more than formatting—it was about credibility, clarity, and professionalism.
Hands-On Network Fundamentals: OSI, TCP/IP, and VPNs in Practice
Exploring OSI, TCP/IP, and practical VPN configurations through hands-on labs to build foundational cybersecurity skills.
Mastering Virtualization for Cybersecurity: Labs Across VMware, WSL, GCP & AWS

Hands-on virtualization labs across VMware, WSL, GCP, and AWS are building foundational skills for offensive and defensive cybersecurity operations.
Building Hands-On Cybersecurity Skills: From MICS to MSAF with MCSI

MCSI labs provide scenario-based exercises that bridge IT fundamentals with advanced cybersecurity practices, building a portfolio of applied skills.
Developing a Cybersecurity Portfolio as an Entry-Level Technician
Hands-on experience is essential for cybersecurity newcomers. MCSI provides a structured, apprenticeship-style training to build applied skills and documentation expertise.

