Tickets, Not Passwords: The Elegant Security System Behind Your Single Sign On
As a Cybersecurity Technician, I know the value of tangible proof of skill. An in-depth report on the Kerberos authentication protocol titled "REPORT – Kerberos Authentication Protocol – v1.0.0" became a cornerstone of my portfolio. Creating this report taught me crucial lessons about technical communication—just as important as technical knowledge itself.
Foundational Knowledge
The Kerberos report began as a graded assignment for the "Computer Security and Systems Management Specialization" course at the University of Colorado. In the "Windows Server Management and Security" module, I had to explain Kerberos in depth. Scoring 500/500 points confirmed my strong grasp of the topic and boosted my confidence.
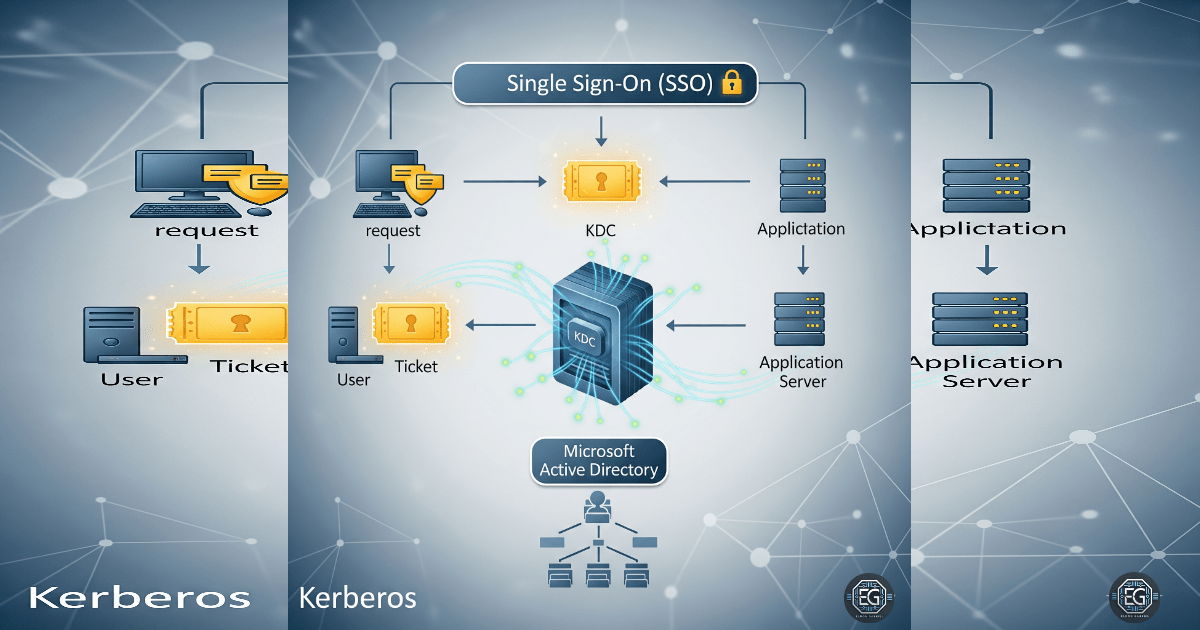
The report breaks down the core problem Kerberos solves: the historical vulnerability of sending plain-text passwords over networks. It explains how Kerberos uses a trusted third party—the Key Distribution Center (KDC)—to issue encrypted, time-limited tickets rather than exposing credentials. This principle is fundamental to modern enterprise security.
Lessons Learned
- Clarity is King: I clearly defined terms like Authentication Server (AS), Ticket Granting Server (TGS), TGT, and ST. I also explained the why behind each component, such as how the TGT enables multiple service tickets without re-authentication—the basis for Single Sign-On (SSO).
- Visuals are Powerful: Diagrams of the Kerberos authentication process helped viewers quickly understand complex, multi-step processes. This shows I can translate theory into clear, easy-to-follow visuals.
- The “So What?” Factor: My report highlights practical relevance, including Kerberos use in Microsoft Active Directory, access to shared drives, internal applications, and the importance of time synchronization to prevent replay attacks.
- Awareness of Vulnerabilities: I included sections on threats like Kerberoasting, Golden Ticket, and Silver Ticket attacks, demonstrating a full understanding of both strengths and risks.
Final Thoughts
The Kerberos report is more than a document—it’s a foundational piece of my cybersecurity portfolio. It demonstrates my ability to learn complex systems, apply them practically, and communicate them clearly. Most importantly, it reflects my dedication to building a strong portfolio and my commitment to breaking into the cybersecurity industry.
Full Report: REPORT – Kerberos Authentication Protocol – v1.0.0