Anonymous access has long been a way for attackers to silently enumerate users, groups, and shares on a Windows system. In this exercise, I hardened a standalone Windows 10 machine by configuring Local Group Policy settings that restrict null session access and deny anonymous logons. The goal: remove unauthenticated pathways into the system and reduce exposure to common enumeration attacks.
Applying the Policy
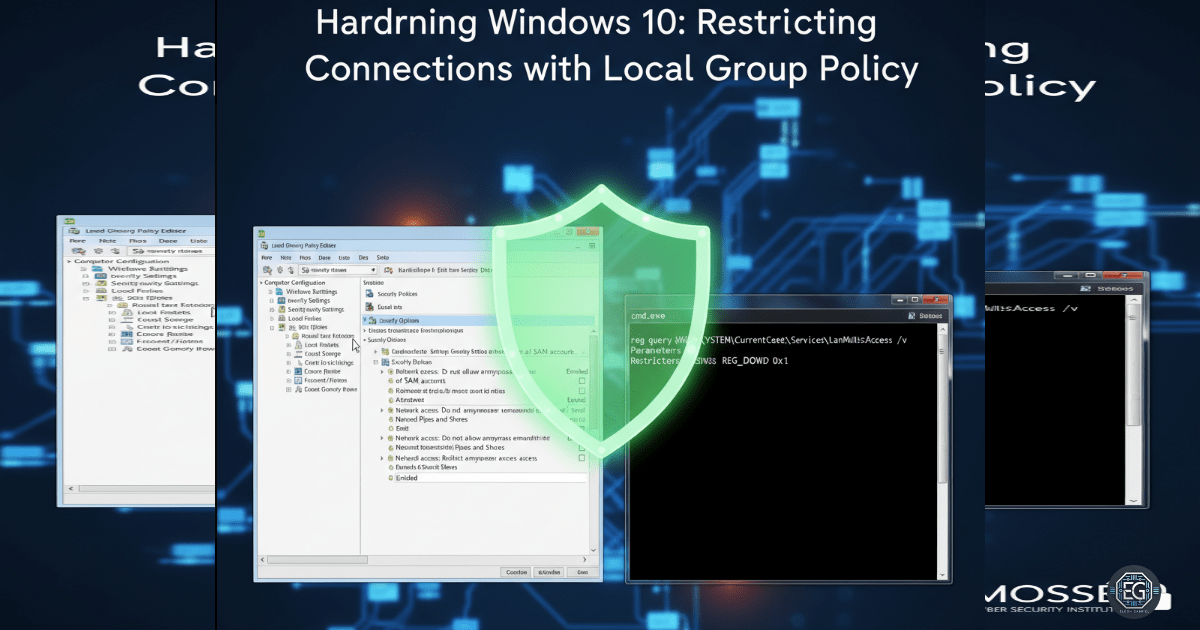
I used Local Group Policy paths to configure two main areas:
Anonymous Access Restrictions
- Path:
Computer Configuration → Windows Settings → Security Settings → Local Policies → Security Options - Policies Configured:
- Network access: Do not allow anonymous enumeration of SAM accounts and shares → Enabled
- Network access: Restrict anonymous access to Named Pipes and Shares → Enabled
User Rights Assignment
- Path:
Computer Configuration → Windows Settings → Security Settings → Local Policies → User Rights Assignment - Policy Configured:
- Deny access to this computer from the network → Guests, Local account
Verification
I verified the settings with the following command:
reg query HKLM\SYSTEM\CurrentControlSet\Services\LanManServer\Parameters /v RestrictNullSessAccess
The output confirmed a DWORD value of 0x1, proving the restrictions were successfully applied.
Why This Matters
Null sessions are often abused by attackers for reconnaissance before launching targeted attacks. By cutting off anonymous access, organizations can significantly reduce their attack surface and comply with baseline hardening standards such as CIS and NIST 800-53.
For non-technical readers: think of this as locking a building’s utility doors so that strangers can’t sneak inside to scope out the layout before attempting a break-in.
Professional Relevance
This exercise reinforces skills aligned to:
NICE Framework – System Administration (OM-SA-001): Applying OS-level security configurations to protect systems from unauthorized access.
ASD Cyber Skills Framework – System Hardening: Implementing security policies that restrict access and reduce system vulnerabilities.
These capabilities directly map to the responsibilities of junior Security Administrators and IT Operations Technicians.
Key Takeaways
Anonymous access restrictions prevent unauthenticated enumeration.
User Rights assignments harden the system against unwanted network logons.
Command-line validation is critical for proving security controls are active.
Local hardening methods scale to enterprise-wide policies via Active Directory GPO.
For the full step-by-step process and deeper insights, see my full report below: