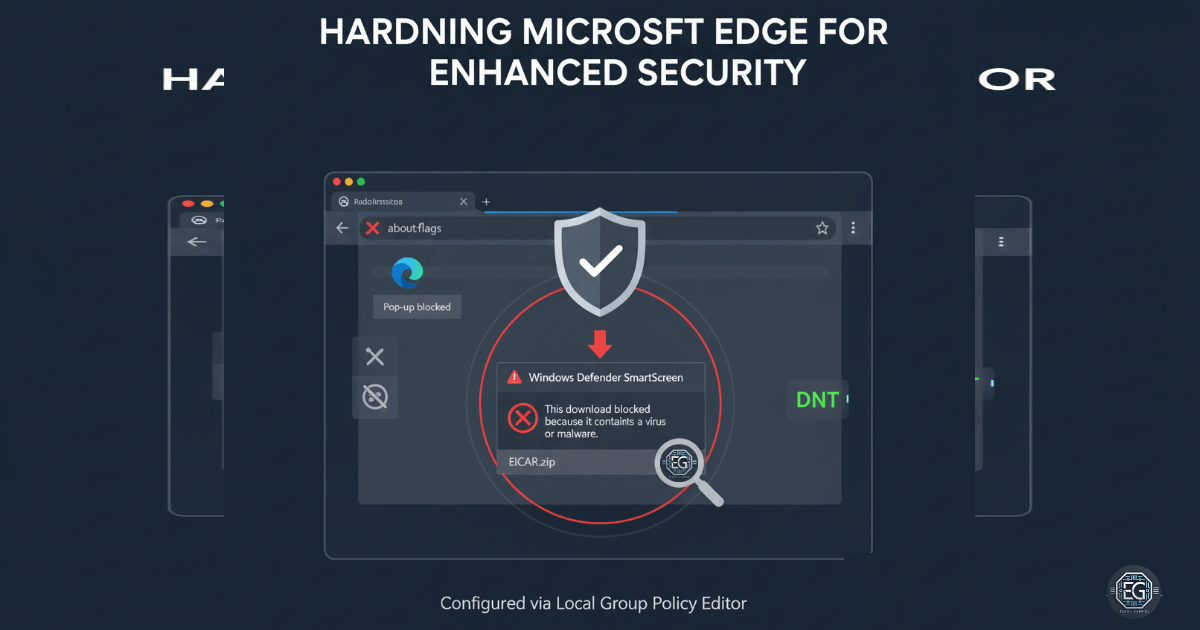
I recently worked on making Microsoft Edge safer. Edge is more secure than Internet Explorer, but adding extra security settings makes it even harder to attack.
Hardening Steps
I used the Local Group Policy Editor to configure key settings:
- Disabled Adobe Flash to remove a common security risk.
- Disabled Developer Tools to reduce misuse.
- Enabled Do Not Track to protect privacy.
- Disabled the Password Manager to keep login info safe.
- Enabled Pop-up Blocker to prevent phishing attempts.
- Enabled Windows Defender SmartScreen to block malicious sites and downloads.
- Prevented access to experimental features (about:flags) to stop policy bypass.
- Configured dangerous site blocking for strict protection.
Validation
After making these changes, I confirmed that SmartScreen was active in Edge. I tested it by trying to download a known malware file (EICAR). SmartScreen blocked it, showing that the hardening measures worked.
Key Lessons
- Turning off unnecessary features reduces vulnerabilities.
- Using built-in protections strengthens security.
- Testing settings ensures they work as intended.
Professional Relevance
Securing browsers helps prevent phishing, stolen passwords, and data leaks. Cybersecurity professionals need to know how to apply and verify these settings to protect users and maintain compliance.