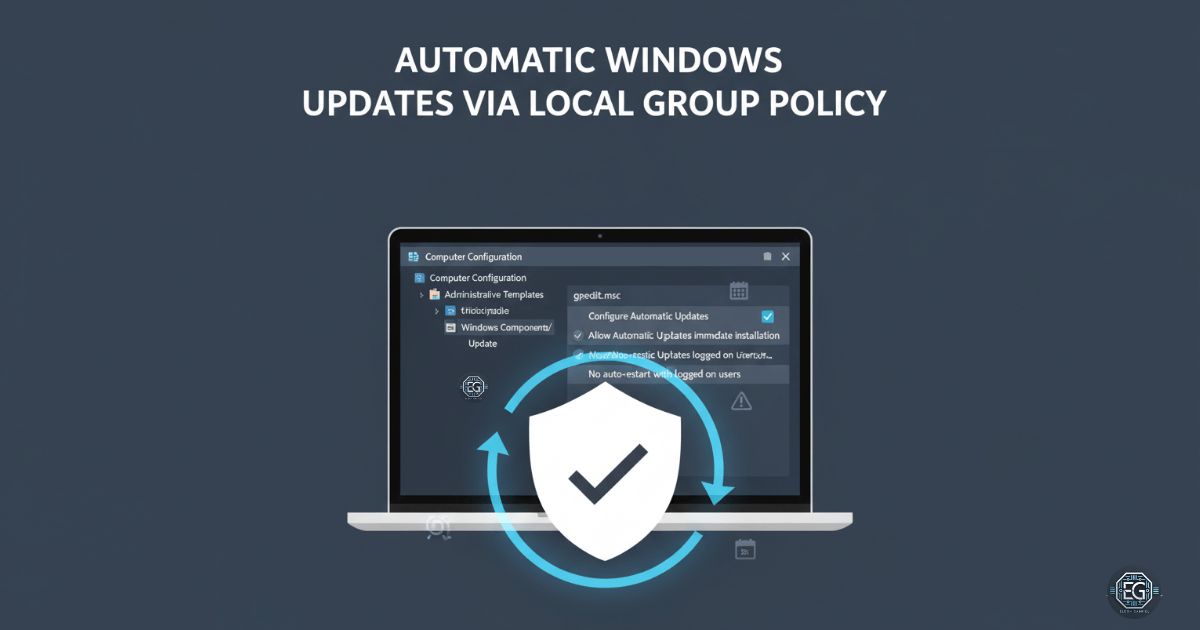
One of the easiest ways for attackers to break into a system is by using unpatched software. If updates are not installed, hackers can use old flaws to get in. In this exercise, I used the Local Group Policy Editor on a Windows 10 computer to make sure updates are installed automatically.
The goal was simple: stay secure while keeping the computer easy to use.
What I Configured
- Turned on automatic updates
- Allowed immediate installation of certain updates
- Stopped driver installs through updates
- Prevented auto restarts when someone is logged in
- Left update features available
- Enabled recommended updates with important ones
Validation
To confirm it worked, I:
- Opened the Local Group Policy Editor (
gpedit.msc) and applied the settings - Ran
gpupdate /forceto apply changes right away - Checked the results with
gpresult /r - Reviewed Windows Update logs
- Captured video recordings for proof
The changes applied immediately, showing that Local Group Policy is a quick way to control updates on a single machine.
Why This Matters
Regular patching is one of the strongest defenses in cybersecurity. It closes the door on new threats before they can cause damage.
The “No auto-restart” rule made the system easier to use, but it also means admins must plan restarts. Without reboots, some updates don’t finish, leaving systems exposed.
In bigger companies, these rules are enforced through Active Directory Group Policy (AD GPO). This allows IT teams to keep hundreds or thousands of computers patched in the same way.
For the full step-by-step process and deeper insights, see my full report below: