I’ve always learned best by doing: hands-on, portfolio-first, and outcome-oriented. From day one, this mindset has shaped how I approach cybersecurity. MCSI became the backbone of my learning, providing the “how” through structured labs, projects, and real-world exercises. At the same time, I supplement that foundation with reputable courses, like the University of Colorado’s Enterprise System Management and Security module, to understand the “why” behind the concepts I’m applying.
This dual-path approach turns every concept into something I can immediately put into practice. The work for both the University of Colorado and MCSI is certified by both institutions, providing recognized credentials that complement my hands-on experience and serve as tangible proof of my skills.
Certifications
| Certification Name | Issuing Organization | Certification |
|---|---|---|
| Lab Setup – Create a Virtual Machine in VMWare | Mossé Cyber Security Institute | View Certificate |
| Lab Setup – Deploy a Virtual Machine in AWS | Mossé Cyber Security Institute | View Certificate |
| Install and configure VM Ware ESXi with Vsphere in Windows and Linux VMs | Mossé Cyber Security Institute | View Certificate |
| Enterprise System Management and Security | University of Colorado | View Certificate |
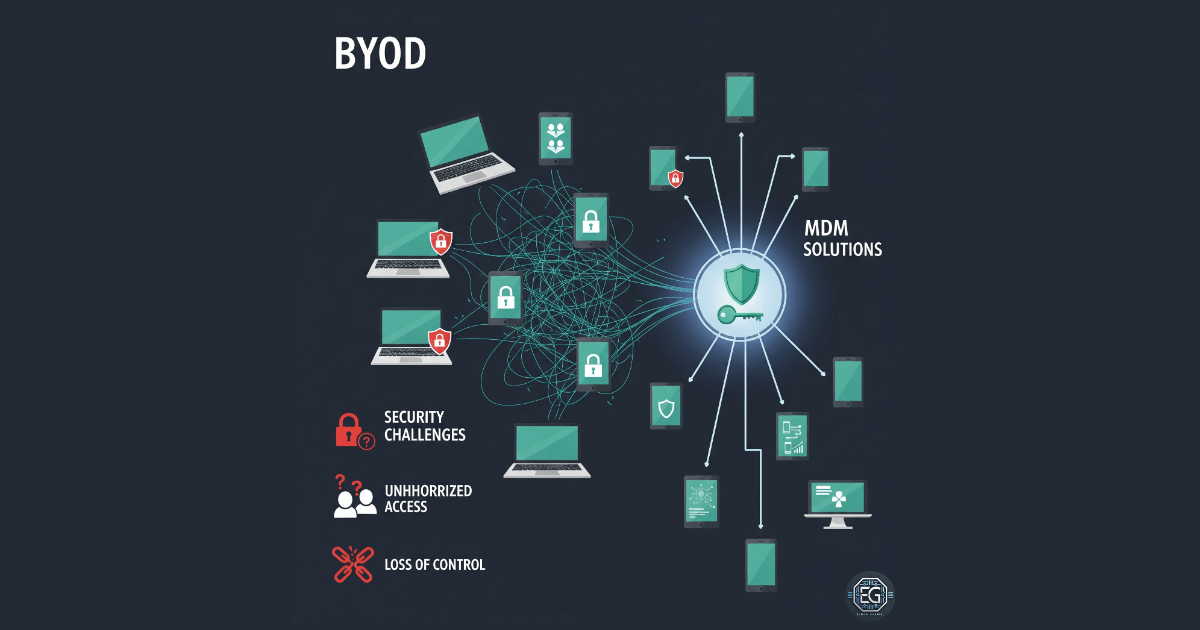
That’s exactly how my BYOD report REPORT – BYOD in Organizations: Security, Challenges, and Strategies – v1.0.1.pdf came to life. What started as a graded assignment evolved into a professional, governance-ready guide. In it, I examine:
- The evolution of BYOD and how organizations respond
- Security risks introduced by personal devices, malware, and lost hardware
- Practical mitigation strategies like network segmentation and Mobile Device Management (MDM)
BYOD Contract Template
To make the report actionable, I created a BYOD Contract Template. This template is not generic — it reflects the real-world application of the report’s recommendations. It covers:
- Device security requirements
- Technical measures like encryption and multi-factor authentication
- Safe procedures for removing company data and revoking access when employees leave
Together, the report and template provide a clear framework for organizations looking to build a secure, adaptable BYOD program.
Why BYOD Matters Today
The rise of remote work has made BYOD a permanent part of modern workplaces. Employees benefit from using familiar devices, improving productivity and satisfaction. But every advantage comes with risk. My goal is to give organizations practical tools to manage those risks without overcomplicating things.
Every report, template, and project I produce follows the same principle: real labs, real skills, real results. These are not theoretical exercises — they are tangible outputs from my learning journey, designed to provide immediate value to real organizations while reflecting the skills and insights I’m building along the way.
Full Report: REPORT – BYOD in Organizations: Security, Challenges, and Strategies – v1.0.1.pdf