Insights
I'm Eldon Gabriel, an ISC² Certified Cybersecurity Professional and AI Dataset Trainer. I build, secure, and optimize IT systems through real-world labs, projects, and research. My expertise spans Windows/Linux administration, network architecture, incident response, and threat analysis, complemented by AI/ML dataset work that sharpens analytical precision. Over 100+ labs and reports demonstrate my practical skills in defending modern IT environments.
Key Influences and Lessons
My journey from business to cybersecurity has been shaped by hands-on technical work and lessons learned from remarkable people along the way. These experiences taught me leadership, resilience, and strategic thinking—skills I now apply to building secure networks, hunting threats, and developing proactive defenses.

George H. Ross
NBC’s ‘The Apprentice’ Judge & Mentor
Instilled disciplined evaluation of risks, persistence, and thorough investigative practices essential for threat hunting and incident response.

Bruny Surin
Canadian Olympic Gold Medalist
Taught discipline, focus, and composure under pressure—applied to high-stakes incident handling and complex security investigations.

Wahida Clark
4x NYT Bestselling Author
Reinforced the importance of clear communication and storytelling to explain complex technical risks to non-technical audiences.

Alex Clark
CEO, Quantum Pigeon Technologies Inc.
Highlighted the value of forward-thinking innovation and staying ahead of emerging technology trends, crucial for proactive cybersecurity defenses.

Stedman Graham
Businessman & Author
Emphasized clarity of purpose and strategic thinking, helping to stay focused and intentional in building cybersecurity expertise and projects.
I’ve also learned from other leaders across industries, each shaping my approach to cybersecurity with lessons in strategic thinking, innovation, and resilience. I bring to every challenge technical rigor, strategic insight, and clear communication. Whether investigating incidents, hardening systems, or assessing risks, I apply a mindset shaped by practical experience, mentorship, and continuous learning.
Cybersecurity Report Highlights

Bridging IT Fundamentals to Cybersecurity Mastery
Reverse Image Search in OSINT Investigations
Performed reverse image searches to analyze images, extract metadata, and practice OSINT skills for verifying authenticity and gathering intelligence.
UTM Kali Linux Shared Folder Guide: Persistent File Sharing for Cybersecurity Labs
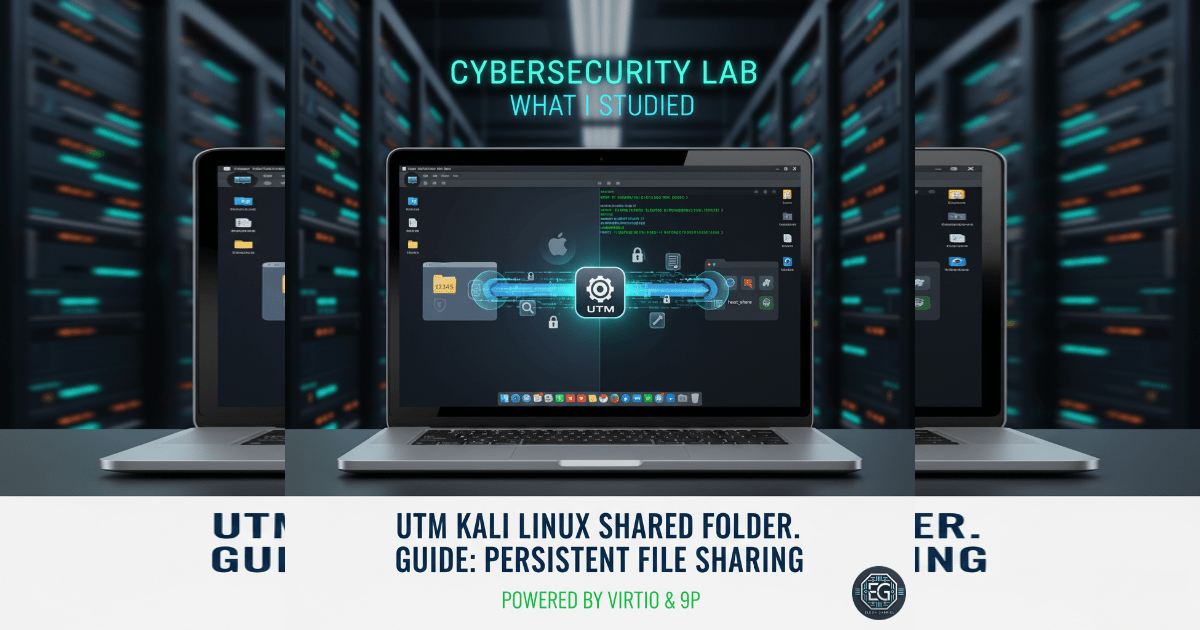
Configured a persistent shared folder between macOS and Kali Linux in UTM to enable reliable cross-platform file transfer for cybersecurity lab environments.
Email Pattern Recognition with OSINT
A hands-on OSINT exercise focused on identifying and validating target email addresses using public PDF documents and email verification tools.
Deploying User Session Lock Policies on a Single Machine

Configured Local Group Policy to enforce automatic session locks, improving Windows endpoint security.
Deploying User Rights Policies on a Single Machine

Configured User Rights Assignment policies via Local Group Policy to enforce least privilege and secure Windows endpoints.
Securing WinRM Configuration with Local Group Policy

Deployed a Local Group Policy Object to securely configure Windows Remote Management (WinRM) for encrypted, authenticated remote administration.
Deploying Local Group Policy to Harden SMB Sessions

A hands-on walkthrough of using Local Group Policy and the Windows Registry to enforce SMB signing, disable SMBv1, and reduce the risk of credential theft and session hijacking.
Deploying Local Group Policy to Strengthen Windows Security

Hands-on exercise applying Local Group Policy settings to harden a Windows 10 workstation and improve system security posture.
Stabilizing Remote Desktop Connections Across Platforms
Resolving complex RDP connectivity issues caused by Domain GPO restrictions and virtual network instability in a macOS UTM environment.
Translating Foreign-Language Data in OSINT Investigations
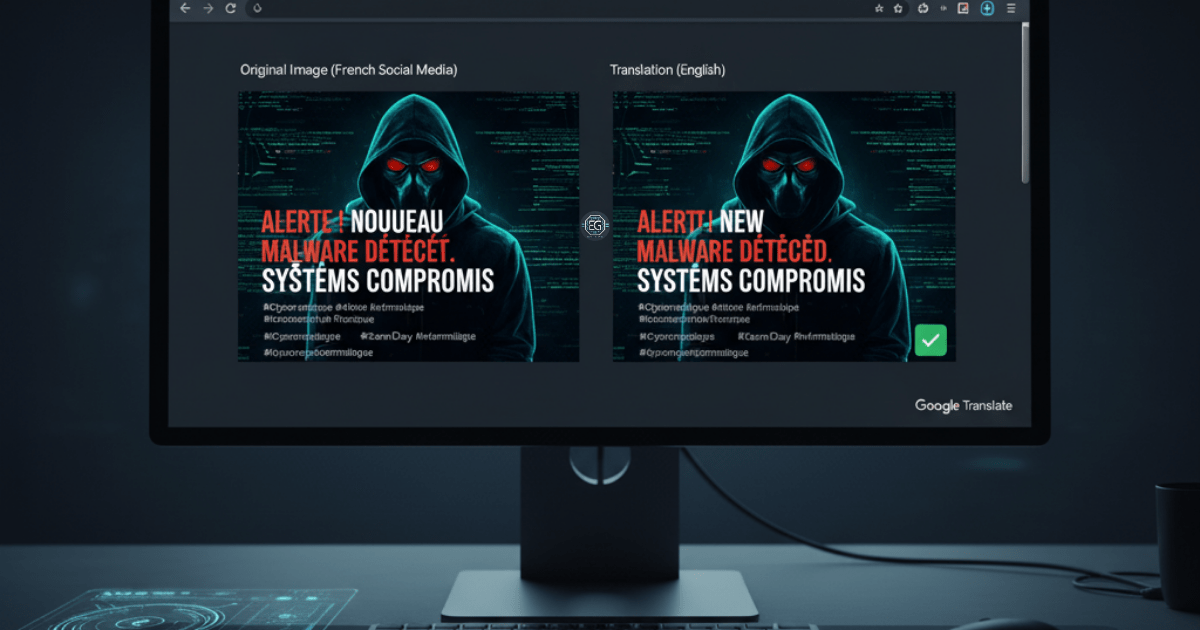
Using translation tools to process and validate foreign-language data from multiple sources including articles, code, images, documents, and webpages.

